When you choose a product—whether it's for work or personal use—you expect it to deliver on its promises and perform as advertised. That's why the OWASP Benchmark is so important; think of it as a rigorous test that measures how well security tools protect your digital information. It’s considered the gold standard for security assessments, providing developers and security professionals with crucial insights into the security posture of their applications and the accuracy of their security testing tools.
We at New Relic understand the value of trust and reliability, which is why we're proud to share some exciting news. New Relic interactive application security testing (IAST) has not just met, but exceeded the highest standards set by this industry test, scoring over 100%. This achievement is a testament to our commitment to keeping your digital environment safe and secure, drawing on our deep-seated knowledge and expertise in application performance monitoring (APM) and now security too.
The significance of accuracy
We know that when it comes to protecting your customers' online activities, you want security that you can truly count on—security that doesn't cry wolf with false alarms. At the heart of our OWASP (Open Worldwide Application Security Project) results is IAST’s unparalleled ability to identify genuine security concerns without being misled by something that looks like a vulnerability but can’t be proven.
While other security testing tools strive to achieve high detection rates, they often mistakenly flag harmless references as vulnerabilities, leading to unnecessary worry and wasted developer cycles. The New Relic IAST solution however has demonstrated an unmatched level of precision in detecting a wide array of the top OWASP vulnerabilities. It's like having a highly skilled security detective who can spot issues that others might miss- which outline the most critical security risks to applications today.
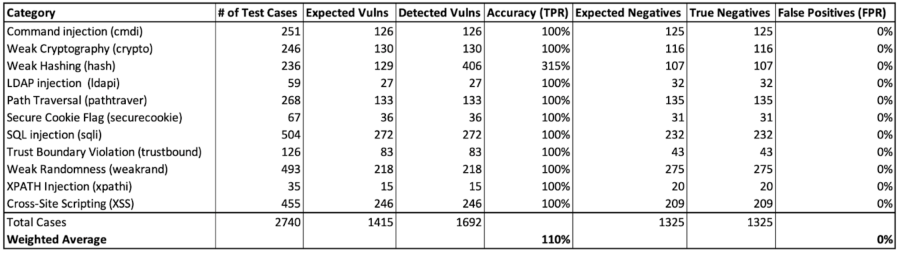
Based on the OWASP v1.2 benchmark New Relic IAST has scored 110% percent in true positives and zero percent in false positives across all 11 categories.
It’s worth noting that we did make some configuration changes to the APM agent to enable low priority instrumentation to allow IAST to be more attentive to the subtlest signs of security risks.
We've put IAST through a rigorous test, the OWASP v1.2 benchmark, and the results speak for themselves: a perfect score in catching real threats and zero mistakes in identifying false ones across 2,740 test cases. With cyber threats becoming more sophisticated, the accuracy of security tools in pinpointing exploitable vulnerabilities is paramount to involving developers as part of the security solution because it’s easy to trust and remediate.
315% in weak hashing
What does scoring over 100% in the weak hashing category really mean? The objective of these test cases is to verify the integrity of the data without needing to store the original data. Unlike encryption, hashing is a one-way function. Tests for weak hashing focus on the ability to detect vulnerabilities in how hashing functions are used, particularly for password storage or data integrity checks. Common vulnerabilities assessed are:
- Use of deprecated or weak hashing algorithms (for example, MD5, SHA-1) that are vulnerable to collisions or preimage attacks.
- Lack of proper salting, making hashed values more susceptible to rainbow table attacks.
- Insufficient iterations of hashing, which can leave hashed values vulnerable to brute-force attacks.
- Misuse of hashing functions or libraries.
- Storing sensitive information with inadequate or no hashing, risking exposure if the data storage is compromised.
One of the key functionalities to our results is that New Relic IAST fully exercises all code paths to serve a particular API, whether that's in the application code or the application framework. Other solutions only focus on the application files but we look at your application holistically. Application files are the building blocks of a specific application, but the framework is a toolset or infrastructure that provides a foundation for developing an application more efficiently by handling many of the lower-level details. Since SHA1 is considered a weak hash algorithm, it is flagged by New Relic’s IAST as it examines the Java runtime framework as seen below:
stackTrace:
'java.security.MessageDigest.getInstance(MessageDigest.java:84)',
'sun.security.pkcs.SignerInfo.verifyTimestamp(SignerInfo.java:588)',
'sun.security.pkcs.SignerInfo.getTimestamp(SignerInfo.java:569)',
'sun.security.pkcs.SignerInfo.verify(SignerInfo.java:329)',
'sun.security.pkcs.PKCS7.verify(PKCS7.java:579)',
'sun.security.pkcs.PKCS7.verify(PKCS7.java:596)',
'sun.security.util.SignatureFileVerifier.processImpl(SignatureFileVerifier.java:283)',
'sun.security.util.SignatureFileVerifier.process(SignatureFileVerifier.java:259)',
'java.util.jar.JarVerifier.processEntry(JarVerifier.java:323)',
'java.util.jar.JarVerifier.update(JarVerifier.java:234)',
'java.util.jar.JarFile.initializeVerifier(JarFile.java:394)',
'java.util.jar.JarFile.getInputStream(JarFile.java:470)', vulnerabilityDetail: [
{
target: 'NONE',
type: 'Weak Hash Algorithm',
detail: 'Unsecured/Weak algorithm used for KeyPairGeneration, Algorithm: SHA-1',
executedQuery: [ 'SHA-1' ],
referentialExecutedQuery: [ 'SHA-1' ],
vulnerabilityState: 'PROBABLE'
}
],IAST can surface the most common dangers but also proves its ability to adapt to new challenges, giving you peace of mind that your digital world is well-guarded.
Addressing benchmark limitations
While the tool's performance is certainly worth celebrating, it's also essential to consider the limitations of the OWASP Benchmark itself. As comprehensive as the benchmark is, it primarily focuses on accuracy in a standardized testing environment. It may not fully encapsulate the complexities of real-world applications or the detection of zero-day vulnerabilities and business logic flaws.
However, scoring over 100% suggests that New Relic’s IAST is not only adept at navigating these standard tests but may also possess advanced capabilities that begin to address these limitations. For instance, its ability to exceed the benchmark hints at potential strengths in detecting more nuanced or previously unidentified vulnerabilities, moving beyond the scope of traditional testing frameworks.
Enhancing security awareness
Another key aspect of IAST’s success is its contribution to security awareness. The performance of IAST in the OWASP Benchmark not only highlights its security acumen but also emphasizes the value of following security best practices. OWASP, recognized for promoting security awareness with comprehensive guidelines and community projects, has inspired the development of IAST. By aligning with these practices, IAST not only secures applications but also educates developers. It provides insights into possible security gaps in comparison to actual vulnerabilities, enhancing developers' understanding of the risks associated with each update. This approach cultivates a more inherently secure development process, making advanced cybersecurity knowledge accessible to all.
Moving forward
When it comes to picking the best technology for your business, it's like choosing a car. You want something reliable, safe, and a good fit for your needs. That's where benchmark testing comes in—it's like taking a car for a test drive to see how well it performs. These kinds of tests can help inform decisions on what technology is best suited for an organization and how vendors can further improve their products.
Testing technology can get complicated. It takes effort, can be resource intensive, and sometimes errors occur. Just like you read reviews and ask questions before making a big purchase, it's smart to look closely at any security product to make sure it's as strong as it claims to be. Transparency is key to evaluating test data and understanding if you can really trust a vendor's claims. These are fundamental concepts—open, repeatable, and defensible results that we can stand behind, so you know exactly what you’re getting.
As we move forward, our goal is to keep exploring and pushing the limits of what our capabilities can address, especially as security challenges become more complex. The recent advancements we've made are a reminder to keep innovating and adapting, no matter what new threats come our way or limitations of current benchmarks.
It's a call to action for developers, security professionals, and organizations to not only leverage advanced tools like New Relic IAST, but also to remain engaged with the broader community in pushing the boundaries of what's achievable in safeguarding our digital world.
Get started today with New Relic IAST
If you have a free New Relic account, you already have access to New Relic IAST if you’re using a supported agent. To learn more, contact your New Relic account representative and get started.
Don’t have a New Relic account yet? Sign up for free today. Your free account includes 100 GB/month of data ingest and one full user.
The views expressed on this blog are those of the author and do not necessarily reflect the views of New Relic. Any solutions offered by the author are environment-specific and not part of the commercial solutions or support offered by New Relic. Please join us exclusively at the Explorers Hub (discuss.newrelic.com) for questions and support related to this blog post. This blog may contain links to content on third-party sites. By providing such links, New Relic does not adopt, guarantee, approve or endorse the information, views or products available on such sites.