The following is a guest post by Alon Berger, Technical Marketing Engineer at Alcide—a cloud-native security platform that provides cloud and Kubernetes discovery, Kubernetes audit and compliance scanner, microservices anomaly detection, and security policies management and enforcement.
The dynamic, distributed, and ephemeral nature of multi-cluster Kubernetes deployments brings new challenges to security and compliance workflows and reporting.
When it comes to troubleshooting, you need to have real-time audit logs analysis.
In-depth audit log examination remains the most established method to identify incongruent activity or strange user behavior. However, manually reviewing audit logs can be a tedious and time-consuming task, especially since the components of a typical Kubernetes deployment are so transient. The need for new and innovative mitigation strategies in such distributed environments is why we teamed up with Alcide to build an integration that notifies you about security and compliance threats in your clusters.
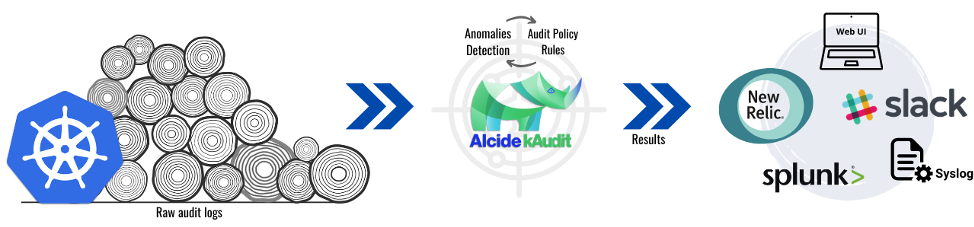
As part of this integration, Alcide introduced kAudit, an automated analytics and forensics module specifically designed to detect and identify suspicious activity, based solely on Kubernetes’ audit logs.
kAudit leverages Alcide's patent-pending AI engine along with machine learning algorithms to process raw audit logs and identify non-compliant, anomalous, and malicious behavior.
These findings can then be pushed to DevOps teams as security-related alerts, or collected for deep investigation and validation by security and audit experts.
This integration between kAudit and New Relic brings comprehensive and in-depth visibility to the New Relic platform, giving you real-time insights and alerts generated by kAudit on potential threats, security incidents, and Kubernetes compliance violations.
Getting Started with kAudit and New Relic
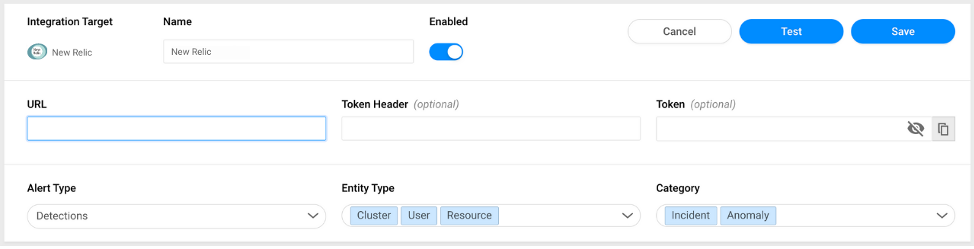
kAudit syncs with New Relic over the New Relic Event API. The HTTP request header must include the X-Insert-Key (the correct Insert API key) as described in the Event API docs.
Once you’re up and running, you can select the desired alerts and entities you wish to receive.
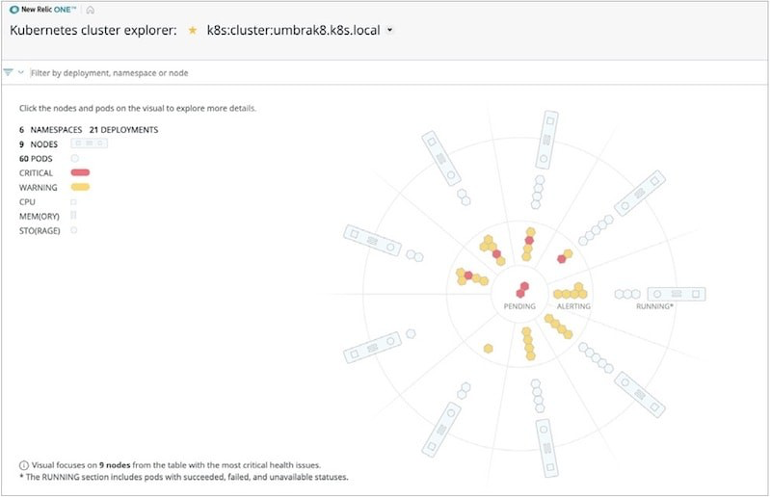
Detect and analyze Kubernetes incidents
With New Relic, you can generate log-based metrics and visualize trends and anomalies occurring in your cluster.
When you add Alcide’s kAudit to the mix you can generate distilled Kubernetes audit logs feed with richer context, in a real-time view of all your operational data.
Alcide’s kAudit solution is a must-have for security teams who need early detection of abnormal activities and anomalies. By automating analytics and forensics, kAudit emancipates both security and DevOps teams from the intimidating task of sifting through raw logs, searching for a root cause. With kAudit and New Relic, you’ll get superior enforcement capabilities.
Here are some of the most common potential threats you can easily detect and prevent with kAudit and New Relic:
- Stolen credentials: Prevent hackers gaining access to Kubernetes-based clusters or pods.
- Misconfigured role based access control (RBAC): Counter lateral attack propagation, privilege escalation, and unauthorized data access or manipulation.
- Exploitation of vulnerabilities in the Kubernetes API server: Avoid bypassing of authentication, authorization, admission control, or validation of cluster admin requests.
- Violations of security policies: Track and spot any divergence from compliance requirements (GDPR, PCI, HIPAA) and best practices.
Policy and compliance enforcement
On top of automated audit analytics and risk detection, there are also compliance and predefined rules to consider and track. Companies deploying Kubernetes-based workloads in many cases also need to align with government and regulatory standards designed to protect financial transactions and private or personal information, such as PCI, GDPR, and HIPAA.
Alcide kAudit automatically assembles, catalogs, and reports on violations of Kubernetes-related compliance best practices. kAudit also offers a variety of easy to use out-of-the-box templates that aid security teams with creating their own customized rules when leveraging New Relic’s enhanced platform capabilities. This ensures full visibility, swift analysis, and optimizations required for an outstanding monitoring experience.
Get started with kAudit and New Relic
Audit logs are a prime way to comprehend the behavior of any cloud-native application orchestrated by Kubernetes. Detecting security risks is a good start; however, we believe that a security solution should also be easy to understand and consumed by more than just the hard-core security experts. By providing the correct user experience, companies can make their Kubernetes logs more accessible, effectively opening a new vista of security possibilities for more professionals. Alcide’s and New Relic’s unified solution offers constant monitoring and real-time analysis of relevant Kubernetes audit logs.
To get started with Alcide and New Relic, sign up for New Relic and get a 14-day free trial of Alcide today.
The views expressed on this blog are those of the author and do not necessarily reflect the views of New Relic. Any solutions offered by the author are environment-specific and not part of the commercial solutions or support offered by New Relic. Please join us exclusively at the Explorers Hub (discuss.newrelic.com) for questions and support related to this blog post. This blog may contain links to content on third-party sites. By providing such links, New Relic does not adopt, guarantee, approve or endorse the information, views or products available on such sites.