What is open-source security?
Open-source security refers to the practice of ensuring that third-party open-source libraries used by an application/system are free from security vulnerabilities. A closely related concept is software composition analysis (SCA), which is a process for identifying and listing all open-source libraries used by an application, and analyzing the versions and security vulnerabilities associated with these libraries.
Many applications use third-party libraries because developing from scratch can be very time-consuming. Furthermore, if those libraries are open source, they may have been tested and leveraged by many developers, making them reliable and bug-free to a large extent. Popular open source libraries also enjoy broad community support and thus benefit from contributions from community members including but not limited to documentation, forums, and feature enhancements.
One example of a popular third-party open-source software is Log4j / SLF4J, with SLF4J serving as a simple facade for various logging frameworks, and Log4J being one of those frameworks. Log4J is used as a logging library by many Java developers because it's highly configurable through external configuration files at runtime and has a dynamic community led by Apache Software Foundation, a non profit organization.
As open-source software continues to grow in popularity, so does the impact of any security vulnerabilities they may contain. It's increasingly important for organizations to ensure the security of their applications that rely on these libraries. As reliable as those open-source libraries may be for the most part, it's inevitable for bugs to slip through the cracks. Moreover, some open-source projects are developed and maintained by a team of volunteers distributed worldwide, adding features and fixing bugs in their free time. Not all open-source communities have the resources or expertise to detect security vulnerabilities, leaving it to users to manage and mitigate security risks.
In December 2021, a zero-day vulnerability (Log4Shell CVE-2021-44228) was discovered in Log4J that caused widespread panic. The National Institute of Standards and Technology (NIST) National Vulnerability Database (NVD) deemed the vulnerability critical and assigned it the maximum base score of 10. Apache Software Foundation described the vulnerability as follows:
“JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints. An attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers when message lookup substitution is enabled.”
This essentially means that Log4J didn’t properly secure the way it used certain Java Naming and Directory Interface (JNDI) features. If an attacker gained control of what gets written in the log messages, they could trick the logging system into reaching out to a malicious Lightweight Directory Access Protocol (LDAP) server controlled by the attacker and inadvertently running harmful code provided by the attacker to exfiltrate data or cause other types of harm.
Due to the ubiquity of Log4J use, remediating this security vulnerability required a tremendous effort from the global IT community. The work required to detect vulnerable systems was substantial and patches needed to be applied to a vast number of systems.
The next section discusses how enterprises can automate open-source security using New Relic.
Reducing time and effort spent on vulnerability identification and remediation
Organizations that do not utilize New Relic capabilities often spend considerable time and effort discovering and documenting all findings in a centralized tracking system, not to mention providing remediation plans and communicating said plans to various teams. This manual approach diverts engineers from their core work and may lead to system downtime as a precaution against high-risk situations.
Continuous runtime software composition analysis
By automating and expediting this process using New Relic Security RX, engineering teams can save valuable time and resources that would have otherwise been spent on manual checks and scans. New Relic software composition analysis (SCA) continuously scans applications and their libraries during application runtime rather than compile time. This enables organizations to proactively identify which applications are impacted by open-source library vulnerabilities and reduces the risk of system downtime due to unaddressed vulnerabilities on an ongoing basis.
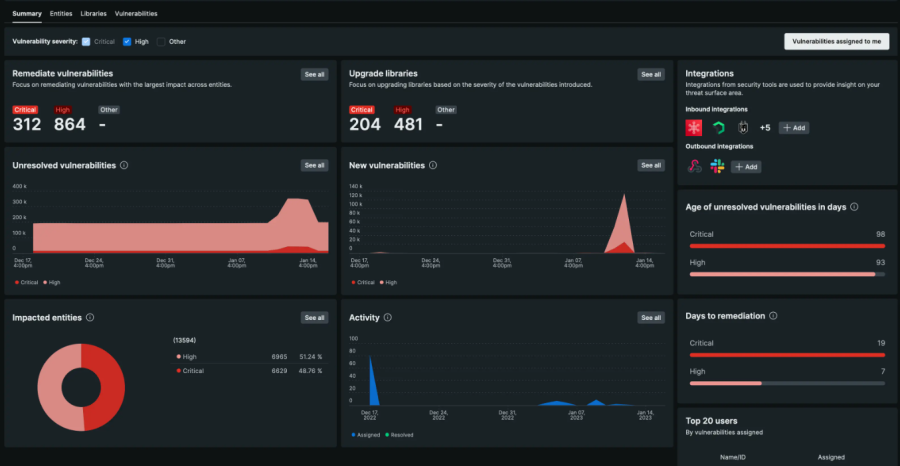
New Relic leverages the same agents that are used for application performance management (APM) to deliver runtime SCA without any additional configuration needed. Therefore, organizations that have deployed New Relic APM agents extensively in their environment will automatically receive runtime SCA coverage across their entire application portfolio. The New Relic APM agents that support Security RX include Java, Node.js, Ruby, Python, and Go, thus providing comprehensive coverage for a wide range of application environments, ensuring that organizations can effectively monitor and manage vulnerabilities across their polyglot architecture.
Common vulnerabilities and exposures (CVEs) detection coverage differs between New Relic APM agents:
| Agent | Minimum Agent Version | CVE Coverage |
|---|---|---|
| AgentJava | Minimum Agent VersionAll supported versions | CVE CoverageJARs |
| AgentNode.js | Minimum Agent VersionAll supported versions | CVE CoveragePackages |
| AgentRuby | Minimum Agent VersionAll supported versions | CVE CoverageGems |
| AgentPython | Minimum Agent Version8.0 or higher | CVE CoverageModules |
| AgentGo | Minimum Agent Version3.20 or higher | CVE CoverageModules |
| AgentPHP | Minimum Agent VersionNot supported | CVE CoverageN/A |
| Agent.NET | Minimum Agent VersionNot supported | CVE CoverageN/A |
Notifying dev teams about security findings
Since New Relic is a cloud-based service, all New Relic users have access to the same curated New Relic Security RX user interface, thus reducing the effort required to document and raise awareness of discovered vulnerabilities.
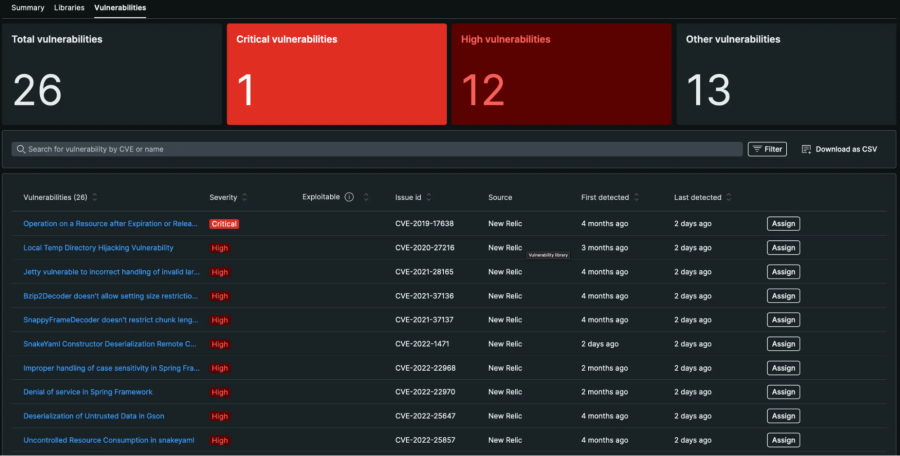
Moreover, the task of remediating a vulnerability can be assigned to a user via the same user interface, which also instructs the assignee on the minimum version of the vulnerable library they could upgrade to in order to resolve the vulnerability. This helps organizations manage large-scale remediation between multiple teams and ownership structures.
When the assigned user has successfully completed the task of patching a vulnerability in a third-party open-source library by upgrading to the New Relic recommended version of that library, the same New Relic Security RX user interface can be used to verify that the vulnerability has been remediated.
New Relic also allows organizations to set up alerts through Slack or a webhook to receive notifications when vulnerabilities of a set severity appear. This ensures development teams are promptly informed about security findings and can take appropriate action to address them. By streamlining communication channels, organizations can further enhance the efficiency of their security processes and reduce the risk of vulnerabilities remaining unaddressed.
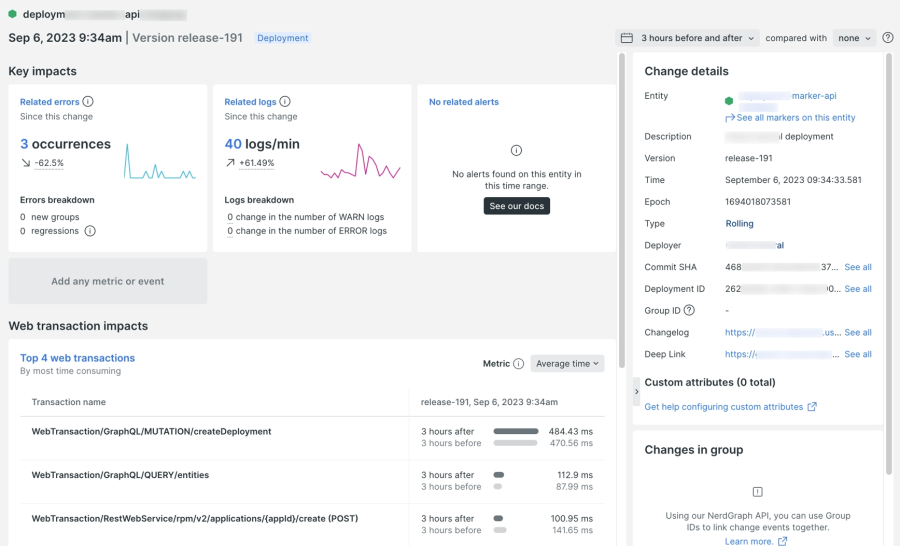
Tracking deployments
Unexpected complications may arise when upgrading a library to resolve a vulnerability. New Relic’s change tracking capability should be used to capture deployments so that their impact on application performance can be analyzed on New Relic curated APM dashboards. New Relic is a one-stop solution for both APM and VM observability that reduces swivel chairing when remediation plans don’t go quite as planned.
Integrating New Relic with other security tools
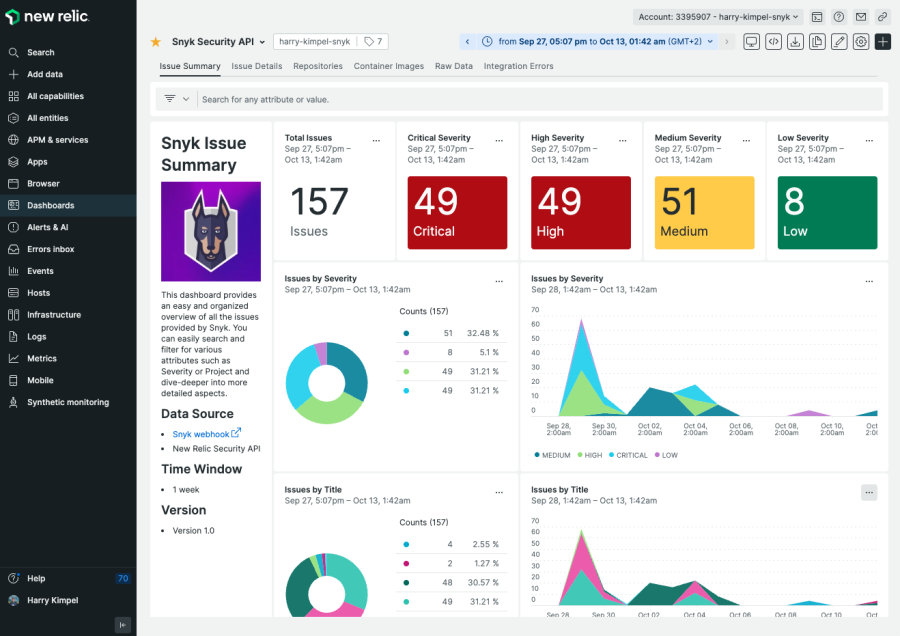
New Relic Security RX capabilities integrate seamlessly with other tools and data sources, providing organizations with a comprehensive view of their security landscape beyond the telemetry provided by New Relic APM agents.
New Relic can report CVEs detected by third-party integrations with tools such as Dependabot, Snyk, Trivy and AWS Security Hub, allowing organizations with an existing deployment of one or more of these tools to hit the ground running with monitoring vulnerabilities in the New Relic platform.
Furthermore, organizations can also send data directly to New Relic through the New Relic security data API. This option is particularly useful when a tool-specific integration doesn't exist or if sending payloads directly to New Relic works best.
Beyond open-source security
While open-source security and SCA are concerned with ensuring third-party open-source applications are secure, interactive application security testing (IAST) is concerned with ensuring your own custom code is secure.
New Relic IAST (in limited preview) is designed for use in non-production environments and provides a powerful security testing technology that can quickly identify exploitable vulnerabilities in custom code. By addressing security risks early in the development process, organizations can reduce the chances of vulnerabilities making their way into production environments. Unlike other IAST solutions that may generate a large number of alarms without providing actionable information, New Relic IAST provides clear proof of exploit and actionable mitigation steps. This is achieved without requiring code changes or disrupting business operations. These insights can inform decision-making processes and help organizations prioritize security investments, tailor security training programs, and refine their security policies and practices.
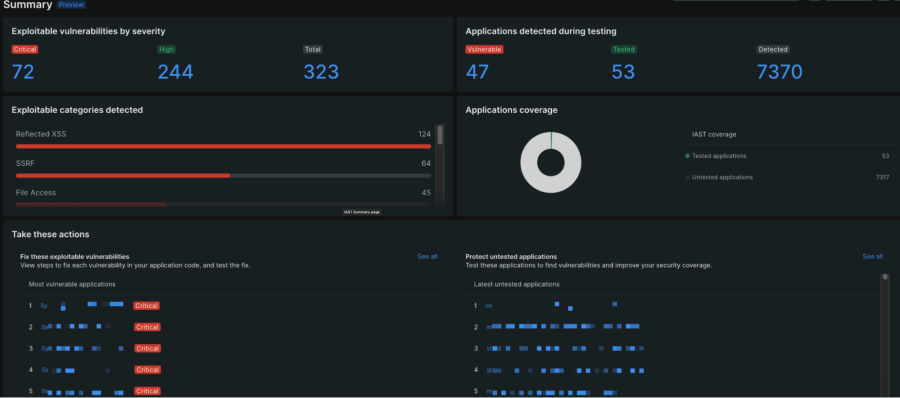
By using both IAST and runtime SCA, organizations can ensure that their entire application stack is effectively monitored and protected against potential security threats. This complementary approach enables organizations to maintain a strong security posture throughout the software development lifecycle (SDLC), reducing the likelihood of security issues making it into production environments.
A more in depth discussion of IAST is outside the scope of this whitepaper.
Summary
Automating open-source security observability is crucial for organizations to effectively manage the risks associated with the use of open-source libraries. By leveraging New Relic's comprehensive capabilities, organizations can streamline vulnerability identification, remediation, and communication processes. This results in more secure applications, efficient use of engineering resources, and reduced risk of system downtime. Additionally, the integration of New Relic's capabilities with existing tools and processes and the provision of actionable insights empower organizations to continuously improve their security posture and stay ahead of emerging threats.
As opiniões expressas neste blog são de responsabilidade do autor e não refletem necessariamente as opiniões da New Relic. Todas as soluções oferecidas pelo autor são específicas do ambiente e não fazem parte das soluções comerciais ou do suporte oferecido pela New Relic. Junte-se a nós exclusivamente no Explorers Hub ( discuss.newrelic.com ) para perguntas e suporte relacionados a esta postagem do blog. Este blog pode conter links para conteúdo de sites de terceiros. Ao fornecer esses links, a New Relic não adota, garante, aprova ou endossa as informações, visualizações ou produtos disponíveis em tais sites.



