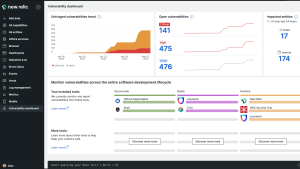
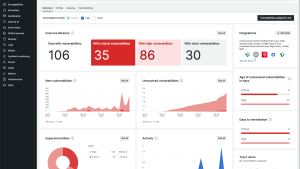
Start communicating effectively across teams to address vulnerabilities with an observability platform that shows you what you need to know quickly, all in one place. With New Relic Security RX, say goodbye to organizational silos and disparate data and hello to vulnerability insights right in the context of your telemetry data.
New Relic Security RX also integrates signals from your preferred third-party security tools with our open ecosystem, while taking advantage of our built-in common vulnerability and exposure (CVE) detection. With one place to both monitor telemetry data and manage vulnerabilities, your development, security, and operations teams can manage security risks across your software stack.
Integrate leading security tools for a unified security view
No matter what tool you use to manage security risks across your tech stack, New Relic makes it simple to manage all your vulnerabilities in one place. We offer over 500 prebuilt integrations that make it easy to instrument data from nearly any telemetry source, including leading security tools that you already depend on to keep you safe. Each of these integrations comes with a quickstart that gives step-by-step instructions for integrating your security data with New Relic.
You can also use the New Relic security API to integrate your security data from any custom source for contextualized Security RX in minutes.
Ready to integrate your security tools? Read on for a list of leading security providers we’ve partnered with to help get you started in minutes.
AWS Security Hub
AWS Security Hub is a cloud security posture management service that performs security best practice checks, aggregates alerts, and can enable automated remediation to help you understand your overall cloud resource vulnerability surface area across AWS accounts.
Importing your AWS Security findings into New Relic allows you to see new vulnerabilities detected by AWS Security Hub, GuardDuty, and Inspector in your account in real time. This enables you to correlate security findings to entities, build out analytics dashboards, and enable alerts on newly detected vulnerabilities for improved mean time to detection (MTTD) and mean time to remediation (MTTR).
Watch this quick demo of how to view vulnerabilities detected by AWS Security Hub in an EC2 instance, and how to get more details and recommendations for how to resolve them without leaving New Relic.
Set up the AWS Security Hub integration
To send AWS security data to New Relic, you’ll need to enable AWS Security Hub on your AWS account and obtain a New Relic license key for the account you want to report data to. Our documentation includes step-by-step instructions on how to import AWS Security Hub, GuardDuty, and Inspector findings into New Relic.
GitHub Dependabot
Github Dependabot can help identify vulnerable open source dependencies, and fix them by automating pull requests with available security updates—allowing you to easily stay protected from known vulnerabilities. Dependabot uses data from the GitHub Advisory Database and the Dependency Graph service to identify insecure dependencies in repositories and creates alerts on your GitHub Enterprise Server instance.
Integrating Dependabot with New Relic allows you to see new vulnerabilities detected by Dependabot right alongside performance and system health in real time, to quickly determine impacted entities, and to create custom dashboards and alerts on newly detected issues for faster vulnerability identification and remediation.
Set up the GitHub Dependabot integration
To import Dependabot data into New Relic, you'll need to send newly detected vulnerabilities to New Relic with a webhook, and you can optionally import previously detected vulnerabilities through a bulk import. Find detailed instructions in our documentation on how to send your vulnerability data with Dependabot based on your preferences.

Snyk
Snyk is a developer security platform that uses industry-leading security intelligence that can help you secure code as it's written, avoid vulnerable dependencies, keep base images secure, and develop secure cloud infrastructure.
By integrating your Snyk data with New Relic, you can automatically correlate issues identified by Snyk with your application, Kubernetes, and other telemetry data for accelerated error resolution. The prebuilt New Relic Snyk quickstart features a customizable dashboard with interactive visualizations for easily-accessible insights and simplified data exploration.
Set up the Snyk integration
To set up the integration between Snyk and New Relic, you’ll need to first create an Azure function app. Head to Snyk’s documentation for more information on how to use Snyk Webhooks to integrate with New Relic, or check out their blog on how to send Snyk vulnerability data to New Relic.
Aquasec Trivy
Aquasec Trivy is a comprehensive security scanner that uses detailed vulnerability and misconfiguration information from the Aqua Vulnerability Database to help DevOps teams gain comprehensive visibility across operating system and programming language packages.
Sending your Trivy scan results into New Relic lets you unify your security findings in one place, query vulnerability events in NRDB, and easily correlate vulnerability findings to entities with real-time updates and prioritization insights.
Set up the Trivy integration
This integration uses the ability of our security data API to process Trivy findings in SARIF. You can find instructions in our documentation on how to ingest your Trivy scan result files using the security data API.
New Relic Security Events API
The security API is a flexible way to send your custom vulnerability or security data to New Relic if you use an integration that isn’t listed above, or if sending data through an API is just a better fit for your workflow. This endpoint interprets security-related data as it is ingested via a simple POST request, and provides a curated user interface for the information.
Send data to our security Events API
You'll need an API license key for the account you want to report data to in order to send vulnerability or other security data using the security data API. You can find detailed instructions on how to transform the output from your existing vulnerability assessment tools into our Security API JSON format, as well as an example POST request in our security data API documentation.
다음 단계
Ready to integrate your assessment tools? If you have a free account or if you are a Data Plus customer, you already have access to New Relic Security RX as long as you are using a supported agent. Standard accounts can enable New Relic Security RX as a single add-on for an additional $0.10/GB over the current data ingest price.
Don’t have a New Relic account yet? Try out our Security RX solution by creating a free account.
이 블로그에 표현된 견해는 저자의 견해이며 반드시 New Relic의 견해를 반영하는 것은 아닙니다. 저자가 제공하는 모든 솔루션은 환경에 따라 다르며 New Relic에서 제공하는 상용 솔루션이나 지원의 일부가 아닙니다. 이 블로그 게시물과 관련된 질문 및 지원이 필요한 경우 Explorers Hub(discuss.newrelic.com)에서만 참여하십시오. 이 블로그에는 타사 사이트의 콘텐츠에 대한 링크가 포함될 수 있습니다. 이러한 링크를 제공함으로써 New Relic은 해당 사이트에서 사용할 수 있는 정보, 보기 또는 제품을 채택, 보증, 승인 또는 보증하지 않습니다.