In today's hyperconnected world, the challenge isn't just about building robust digital platforms; it's about ensuring they remain secure against evolving threats. With each line of code written, each module integrated, and each update released, the potential for vulnerabilities also grows. Traditional Security RX, while valuable, often finds itself playing catch-up, reacting to threats rather than anticipating them. Continuous Security RX, on the other hand, aligns more closely with the rhythm of software development, offering real-time, iterative, and proactive measures.
In this blog, you'll learn:
- The foundational concepts of continuous Security RX
- Key components like scanning, assessment, and remediation
- The tangible benefits from a development and business perspective
- Tips and strategies for effective implementation in your development process
Key components of continuous Security RX
Continuous Security RX has three main components.
- Scanning
- Assessment
- Remediation
Each serves a distinct purpose, yet, when combined, they offer a holistic defense strategy for today's evolving digital threats.
Continuous vulnerability scanning
At its core, vulnerability scanning is the automated process of proactively identifying security vulnerabilities in software applications. In the dynamic world of software, where deployments can occur multiple times a day, scanning in real-time ensures that security efforts keep pace with development. This isn't about merely finding vulnerabilities; it's about staying ahead. Automation in scanning, for instance, allows for non-stop monitoring, ensuring that even in the vastness of codebases, vulnerabilities don't slip unnoticed.
Continuous vulnerability assessment
If scanning identifies vulnerabilities, assessment contextualizes them. It's essential to understand not just the presence of a vulnerability, but its potential impact, severity, and the associated risks it brings to an application's unique environment. Employing a combination of automated tools and manual oversight, techniques range from dependency checks to static and dynamic code analysis. The primary benefit of regular assessments is the ability to prioritize. It ensures that both developers and security teams understand vulnerabilities and can channel their efforts effectively, focusing on the most pressing threats.
Vulnerability remediation
Remediation is the culmination of the scanning and assessment processes, representing the actionable phase where identified vulnerabilities are addressed and resolved. The challenge often isn't just about fixing a vulnerability but determining which vulnerabilities to address first. Using insights from assessments, teams can strategize on addressing high-impact vulnerabilities promptly. By integrating remediation strategies into development processes, like the CI/CD pipeline, teams can not only address vulnerabilities but also create systems less prone to them in the future.
The following image shows the Security RX in New Relic.
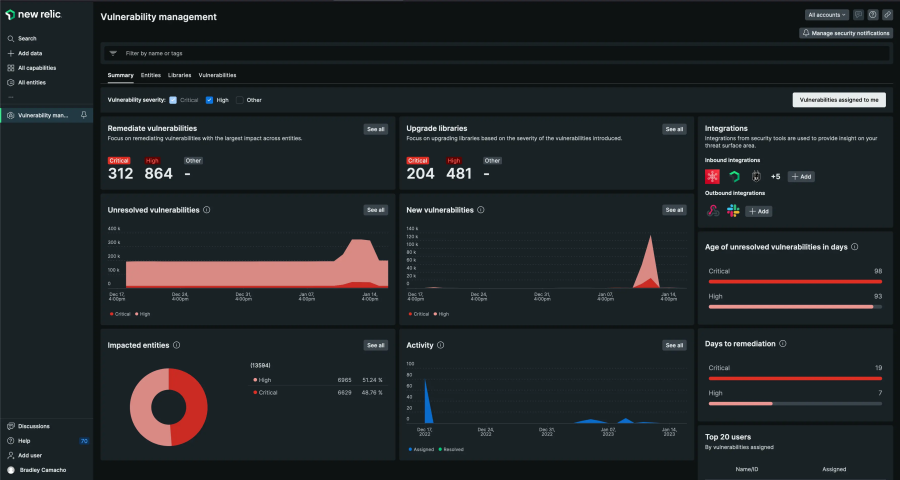
The value of continuous Security RX
Ensuring your software's resilience against potential threats is as vital as its functionality. This is where continuous Security RX shines as it helps balance proactive security needs with the fast pace of agile development.
Enhanced threat detection and prevention
Through continuous scanning, vulnerabilities are identified almost as soon as they appear, ensuring software changes don't introduce unnoticed risks. This proactive approach drastically reduces the chances of exploitation, allowing developers to address issues before they escalate.
Improved risk management and compliance
Regulations like the General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA), and Payment Card Industry Data Security Standard (PCI DSS) demand high levels of cybersecurity. Continuous Security RX helps meet these standards, not just for legal compliance but also to build trust with users. This trust is vital because a single security breach can damage an organization's reputation significantly.
Cost-effective security measures
Addressing security flaws early on is more efficient and cost-effective than managing a major security breach. Continuous monitoring ensures that organizations can prioritize their resources effectively, focusing on the most pressing vulnerabilities first.
Continuous improvement and adaptability
Security isn't static; it evolves. Every detected vulnerability provides an opportunity to learn and enhance security measures. As cyber threats change, the defenses against them need to be agile and robust. Continuous Security RX ensures that these defenses are always up to date, providing a dynamic shield against the evolving threat landscape.
In essence, Continuous Security RX offers a holistic approach, combining proactive defenses with the ever-changing demands of software development and the broader business landscape.
Implementing continuous Security RX
- Establish a Comprehensive Program: Start by auditing your current systems to identify vulnerabilities and assess risks. From this, draft a clear Security RX program detailing roles, responsibilities, and KPIs. Regularly adjust based on new threats and project needs.
- Select Tools and Automate: Choose tools that integrate with your development environment and support real-time feedback. Automation is essential. With tools like New Relic's security workflow, automated scans can be scheduled frequently, ensuring consistent vulnerability checks.
- Facilitate Communication: Create definitive channels for vulnerability reporting. When issues arise, promptly notify the concerned parties with actionable insights. Maintain regular reports for both technical teams and higher management to keep all stakeholders informed.
- Integrate with Broader Security Practices: Combine continuous Security RX with other security protocols like incident response and patch management. Using New Relic's integrations, sync your vulnerability data with other systems, providing a cohesive security overview.
- Prioritize Continuous Education: Keep your team updated on emerging cybersecurity trends. Organize training sessions and webinars to ensure they're equipped with the latest knowledge and best practices.
- Iterate Based on Feedback: Continuously refine your Security RX approach. Incorporate feedback from developers and ensure security is an integrated part of the development process, not an add-on.
Conclusion
Continuous Security RX is essential in today's fast-paced digital landscape. By proactively addressing security threats, developers can ensure the safety of their software applications. Leveraging tools like New Relic enhances this approach, solidifying a robust security foundation for all software projects.
Próximos pasos
Monitor your vulnerabilities now. To get started:
Las opiniones expresadas en este blog son las del autor y no reflejan necesariamente las opiniones de New Relic. Todas las soluciones ofrecidas por el autor son específicas del entorno y no forman parte de las soluciones comerciales o el soporte ofrecido por New Relic. Únase a nosotros exclusivamente en Explorers Hub ( discus.newrelic.com ) para preguntas y asistencia relacionada con esta publicación de blog. Este blog puede contener enlaces a contenido de sitios de terceros. Al proporcionar dichos enlaces, New Relic no adopta, garantiza, aprueba ni respalda la información, las vistas o los productos disponibles en dichos sitios.



