In the fast-paced world of software development, engineers are often flooded with alerts about security vulnerabilities, each tagged with a severity rating that screams for attention. Yet, these severity-based ratings can lead to wasted time and effort, as they don't always reflect the true risk or exploitability of an issue. It's a common pain point: understanding what really demands immediate action because we’re all drowning in common vulnerabilities and exposures (CVEs).
That's why we're shifting the focus towards a more developer-centric approach to Security RX—one that cuts through the noise and pinpoints the vulnerabilities that truly matter to your organization. Using a data-driven approach that allows both security teams and engineers to have a more nuanced understanding of what needs attention that takes into account not just the severity, but what's loaded at runtime, the likelihood of exploitation, proof of the exploit, and its usage in active malware campaigns.
The shortcomings of severity-based prioritization
Severity scores such as those provided by the Common Vulnerability Scoring System (CVSS) have been invaluable to security teams, but they have their limitations. A "critical" severity score doesn’t necessarily mean a vulnerability is being actively exploited or even that it’s exploitable in a particular environment. As a result, security teams spend considerable effort on custom processes to augment their scan-based tools with this type of detail from multiple sources only to find by the time they provide a prioritized list to the dev teams, the information is stale. In other cases they simply go just on severity where teams expend significant resources patching critical vulnerabilities that, in reality, pose a lower risk than some "high" severity vulnerabilities.
A more strategic approach: Weighing severity, EPSS, proven exploit paths, and known ransomware
Our new approach to prioritization refines the focus for engineers and security teams alike. We consider vulnerability severity alongside actionable intelligence from Exploit Prediction Scoring System (EPSS) forecasts and active exploit data from resources like the CISA KEV catalog. This strategy ensures that your team channels its efforts on the threats that pose a tangible risk to your applications that depend heavily on open-source packages.
Interactive application security testing (IAST) further sharpens this focus. By revealing actual exploit paths, IAST guides us to the vulnerabilities that aren’t just theoretical but truly exploitable in your custom code. This integration streamlines your team's work, allowing you to tackle the most critical security issues first and fortify your software's defenses effectively.
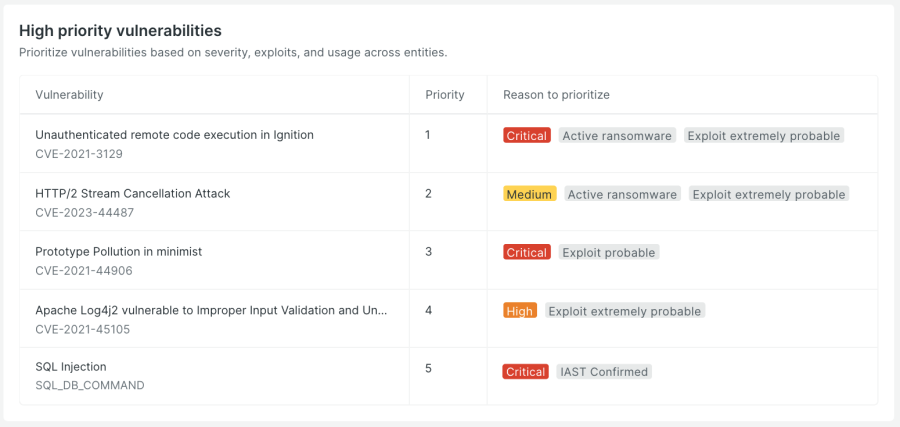
Prioritize vulnerabilities based on severity, exploits, and usage across entities.
The weighted system we’ve added considers four key elements to provided an objective measure with input from various external data points such as:
- CVE severity: The established baseline for the potential impact of a vulnerability.
- Exploit Prediction Scoring System (EPSS): A predictive model that estimates the likelihood of a vulnerability being exploited in the wild.
- Known ransomware associations: Information on whether a vulnerability is being used actively as part of a ransomware campaign, as cataloged by agencies like CISA.
- IAST exploitable vulnerability: A real-time testing method that identifies vulnerabilities with actual exploit paths in running applications, highlighting issues that aren’t just theoretically dangerous but practically exploitable.
The benefits of a weighted prioritization system
Our tailored prioritization system is a powerhouse allowing you not only to use the New Relic platform as a source of data but also third-party security tools that allow your teams to maximize their security impact through:
- Laser-focused resource allocation: Zero in on the vulnerabilities most likely to be exploited, ensuring your security team's efforts pack the biggest punch.
- Proactive defense: By homing in on vulnerabilities already in the crosshairs of known ransomware or in the new version of your application that's about to be deployed, you can shore up defenses before they result in a breach.
- Adaptive security: With the ability to swiftly recalibrate priorities based on the latest intelligence, your security posture remains resilient and responsive, no matter how the digital winds shift.
Conclusion
Our journey helping organizations adopt a DevSecOps culture is driven by our commitment to reducing alert fatigue and easing the burden on developers. We're continuously seeking ways to enhance our prioritization process with additional insights—from package quality to supply chain integrity and beyond. These improvements are aimed at illuminating the most pressing risks, allowing developers to focus their efforts on enhancing the security and robustness of their applications.
Weaving EPSS, data on exploited vulnerabilities, and active malware campaigns into our prioritization process, we empower organizations to shore up their defenses where it counts the most. As we hone our methods and tools, we encourage everyone to embrace this new developer-centric way to tackle Security RX.
Keep an eye out for further updates as we deepen our commitment to fortifying security for developers and security organizations across the globe. By joining forces, we're not just strengthening defenses—we're shaping a more secure future for the digital world.
다음 단계
Get started today with New Relic Security RX
If you have a free New Relic account, you already have access to New Relic Security RX if you’re using a supported agent. To learn more, contact your New Relic account representative and get started.
Don’t have a New Relic account yet? Sign up for free today. Your free account includes 100 GB/month of data ingest and one full user.
이 블로그에 표현된 견해는 저자의 견해이며 반드시 New Relic의 견해를 반영하는 것은 아닙니다. 저자가 제공하는 모든 솔루션은 환경에 따라 다르며 New Relic에서 제공하는 상용 솔루션이나 지원의 일부가 아닙니다. 이 블로그 게시물과 관련된 질문 및 지원이 필요한 경우 Explorers Hub(discuss.newrelic.com)에서만 참여하십시오. 이 블로그에는 타사 사이트의 콘텐츠에 대한 링크가 포함될 수 있습니다. 이러한 링크를 제공함으로써 New Relic은 해당 사이트에서 사용할 수 있는 정보, 보기 또는 제품을 채택, 보증, 승인 또는 보증하지 않습니다.



